Last Updated on January 30, 2024 by Ankit Kochar

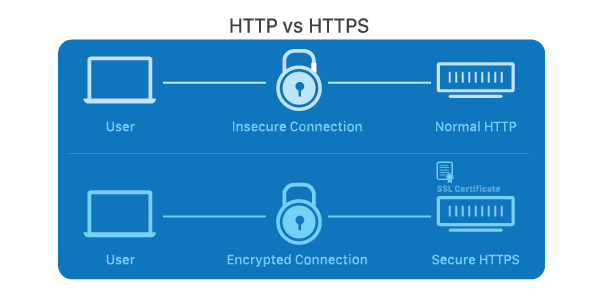
Secure Socket Layer (SSL) is a cryptographic protocol designed to provide secure communication over a computer network, most commonly the internet. It ensures the confidentiality and integrity of data exchanged between a user’s web browser and a website server. SSL operates by encrypting the data transmitted, making it unreadable to anyone attempting to intercept the information.
Originally developed by Netscape, SSL has become a fundamental component of modern web security. It establishes a secure connection through a process called the SSL Handshake, where the server and client authenticate each other and agree on cryptographic algorithms and keys. SSL is now succeeded by its successor, Transport Layer Security (TLS), although the terms SSL and TLS are often used interchangeably.
What is Secure Socket Layer (SSL)?
Secure Socket Layer (SSL) is a cryptographic protocol that provides a secure and encrypted connection between a client (such as a web browser) and a server (such as a website). Its primary purpose is to ensure the confidentiality, integrity, and authenticity of data exchanged between these two entities over the internet. SSL achieves this by using encryption algorithms to scramble the data, making it unintelligible to anyone intercepting the communication.
Understanding Secure Socket Layer (SSL) Protocols
There are various protocols in a SSL layer. Let us understand each of these protocols in depth.

SSL Record Protocol
At the heart of the SSL protocol stack lies the SSL Record Protocol. This protocol furnishes two essential services to SSL connections: confidentiality and message integrity. The SSL Record Protocol ensures that data transmitted between a client and a server remains confidential and that any tampering or unauthorized modification of the data is detected.

The application data is divided into fragments, which undergo compression before encryption. To bolster integrity, a Message Authentication Code (MAC) is generated using algorithms like SHA (Secure Hash Protocol) and MD5 (Message Digest), and it’s appended to the compressed fragment. Encryption of the data follows, and finally, an SSL header is attached to the encrypted data.
Handshake Protocol
The Handshake Protocol is instrumental in establishing secure sessions between clients and servers. This protocol enables both entities to authenticate each other by exchanging a series of messages. The Handshake Protocol unfolds across four phases:

1. Phase 1: Both the client and the server initiate the exchange by sending hello packets. These packets contain information about the IP session, cipher suite, and protocol version to enhance security.
2. Phase 2: The server responds by transmitting its certificate and server-key-exchange. This phase culminates with the server sending a Server-hello-end packet.
3. Phase 3: The client, in turn, replies to the server’s messages by sending its certificate and client-exchange-key.
4. Phase 4: Change-cipher suite takes place in this phase. After this, the Handshake Protocol concludes, setting the stage for secure communication.
Change-Cipher Protocol
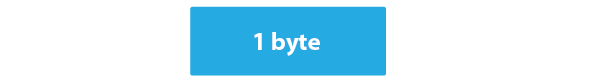
The Change-Cipher Protocol, closely tied to the SSL Record Protocol, plays a pivotal role in transitioning from the pending state to the current state. Until the Handshake Protocol is completed, the SSL record output remains pending. The Change-Cipher Protocol consists of a single 1-byte message, with the sole purpose of moving the pending state to the current state.
Alert Protocol
In the intricate web of SSL communication, the Alert Protocol serves as the bearer of SSL-related alerts to the peer entity. Each message within this protocol is composed of two bytes, contributing to the notification of events and issues that affect the SSL connection.
These alerts are classified into two levels:

1. Warning (level 1): These alerts do not disrupt the connection between sender and receiver. Examples include alerts for a bad certificate, absence of a certificate, certificate expiration, and more. The "close notify" alert signifies the sender’s intention to cease sending messages in the connection.
2. Fatal Error (level 2): Fatal alerts lead to the termination of the connection, rendering it irreparable. Instances include a handshake failure, decompression failure, illegal parameters, and the receipt of an unexpected message.
The second byte in the Alert Protocol serves as a descriptor of the specific error or alert encountered.
Understanding Secure Socket Layer (SSL) Handshake
The foundation of SSL lies in the SSL handshake, a process that establishes a secure connection between a client and a server. The handshake involves a series of steps:
1. Client Hello: The client initiates the handshake by sending a "Client Hello" message, which includes supported SSL/TLS versions and encryption algorithms.
2. Server Hello: The server responds with a "Server Hello" message, selecting the highest mutually supported SSL/TLS version and encryption algorithm.
3. Certificate Exchange: The server presents its digital certificate, which contains its public key and other relevant information. The client validates this certificate against trusted certificate authorities (CAs).
4. Key Exchange: Both client and server agree on a session key using asymmetric encryption, which will be used for symmetric encryption during data transmission.
5. Cipher Suite Agreement: The client and server agree on a cipher suite that includes encryption algorithms, hash functions, and key exchange methods.
6. Finished: The handshake concludes with a "Finished" message, indicating that subsequent data will be encrypted using the agreed-upon parameters.
Understanding Secure Socket Layer (SSL) Encryption
The core purpose of SSL is to encrypt the data being transmitted between the client and the server, ensuring its confidentiality. This encryption prevents eavesdroppers from intercepting and deciphering sensitive information. SSL uses symmetric encryption (faster but requires both parties to have the same secret key) and asymmetric encryption (slower but facilitates secure key exchange) to achieve this.
SSL Certificates and Certificate Authorities (CAs)
SSL certificates play a pivotal role in establishing trust between clients and servers. These certificates are issued by Certificate Authorities (CAs), organizations responsible for verifying the legitimacy of the entities requesting certificates. The certificate includes the server’s public key and is digitally signed by the CA, ensuring the certificate’s authenticity. Browsers and clients have a pre-loaded list of trusted CAs to validate these certificates.
Evolution into TLS
SSL has evolved over time and has been succeeded by Transport Layer Security (TLS). TLS builds upon the principles of SSL, with the latest version being TLS 1.3. While the core concepts remain the same, TLS has improved security and performance features, better cryptographic algorithms, and enhanced resistance to vulnerabilities found in earlier SSL versions.
Importance of SSL/TLS in Today’s Digital World
1. Data Privacy: SSL/TLS encryption ensures that sensitive data, such as credit card information and personal details, remains private and cannot be intercepted by malicious actors.
2. Trust and Authenticity: SSL certificates establish the legitimacy of websites and assure users that they are interacting with the intended server rather than a malicious impersonator.
3. SEO and Browser Compatibility: Search engines like Google consider SSL/TLS as a ranking factor. Additionally, many modern browsers flag non-secure websites, influencing user trust and accessibility.
4. Regulatory Compliance: Many industries, such as finance and healthcare, are bound by regulations that mandate the use of encryption for data protection. SSL/TLS helps organizations comply with these regulations.
Conclusion
In conclusion, Secure Socket Layer (SSL) stands as a cornerstone in ensuring the security and privacy of data transmitted over the internet. Its encryption protocols have become an industry standard for securing online transactions, sensitive information exchanges, and protecting users’ privacy. While SSL has evolved into Transport Layer Security (TLS), the fundamental principles of encrypting communication remain essential for building trust in the digital age. As technology advances, SSL/TLS continues to adapt, providing a secure foundation for the vast landscape of online interactions.
Frequently Asked Questions (FAQs) Related to SSL
Here are some of the frequently asked questions related to SSL and online security.
Q1: What is the difference between SSL and TLS?
A1: SSL (Secure Socket Layer) and TLS (Transport Layer Security) are cryptographic protocols that provide secure communication over a network. TLS is an updated and more secure version of SSL. The terms are often used interchangeably, but TLS is the modern standard for securing data transmission.
Q2: How does SSL ensure the security of data?
A2: SSL ensures data security through encryption. During the SSL Handshake, the server and client agree on cryptographic algorithms and exchange keys. This process encrypts the data transmitted between them, making it unreadable to anyone attempting to intercept the information.
Q3: Is SSL still secure, or should I use TLS?
A3: While SSL is considered less secure than TLS, it can still provide a level of security. However, it is recommended to use the latest version of TLS for better protection against evolving cyber threats. Most modern systems and browsers support TLS, and websites are encouraged to upgrade their security protocols.
Q4: How can I check if a website is using SSL/TLS?
A4: Check the URL of the website. If it begins with "https://" instead of "http://," the website is using a secure connection. Additionally, most browsers display a padlock icon in the address bar to indicate a secure connection.
Q5: Can SSL protect against all types of cyber threats?
A5: SSL primarily focuses on encrypting data during transmission, providing protection against eavesdropping and data interception. However, it does not protect against all types of cyber threats, such as malware or phishing attacks. A holistic cybersecurity strategy is recommended for comprehensive protection.


